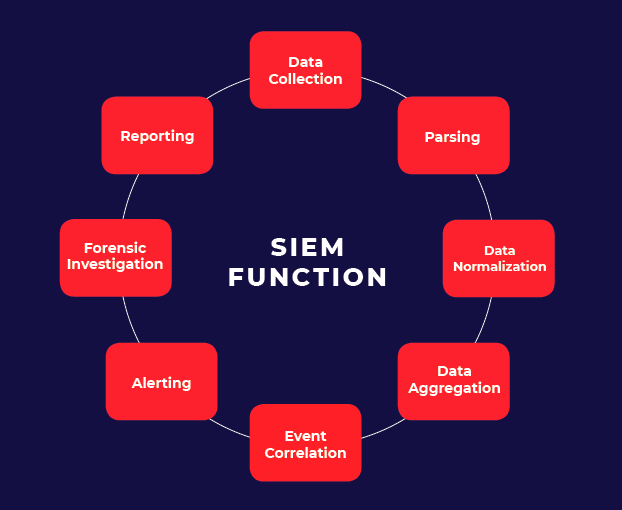
As a function of the SIEM itself, logs from your environment are gathered into one central location and displayed together to provide full context to host activity.
SECURITY INFORMATION AND EVENT MANAGEMENT
The partnership that builds-up your team, operationalizes your SIEM, and betters your security posture in the long run.
The security landscape is always changing, and high-level security architects are hard to come by. Products are helpful, but it is the mapping of the products, technology and organizing business politics, policies, compliance requirements, current teams, and objectives that matter.
Your information security needs to be done correctly, quickly, and professionally to ensure you have the highest visibility into your environment.
And while partnerships for pen testing and tabletop services are crucial to the development of your security operations, your partnership with a SIEM service provider will provide the hub for all your security activity.
What Is a SIEM?
Security Information and Event Management (SIEM) is a software and solution for logging, monitoring, alerting, anticipating, correlating and visualizing security-related events and information garnered from networked devices. Plainly, SIEM is a combination of both processes and tools, or products.
SIEM converges various cybersecurity practices with rich contextual information via an aggregated security data repository for network logs, correlation engines, event modelers with alarm customization, ticketing, predictive analyzers and a decision support system that can be augmented with big data analytics for on-demand reporting and compliance.
What is Cloud-based SIEM?
Cloud-based SIEM is provided as a service for organizations. The SIEM platform with its various tools are in the cloud. This means no hardware and lower operational costs across the board. Monitor, analyze, and update your SIEM from one cloud access point.
SIEM Tools
A few known platforms and software. (Not a complete list):
Who Uses a SIEM?
Although predominantly utilized by sectors like the government, finance, healthcare, manufacturing and law, any organization that is vulnerable to cybersecurity threats like malware, ransomware, zero-day exploits, cyber warfare and insider threats, should implement SIEM (preferably at the beginning or early stages of business expansion). Compliance requirements like GDPR, NIST, audits and log management are another reason.
Do startups need a SIEM?
Cyber attacks do target small businesses. However, many startups can do without a SIEM if data backup policies and general security best practices are followed well. As the business scales up, SIEM should definitely be considered.
SIEM Definitions
Although others in the industry may use these terms in different ways, here is a brief list of a common words you may come across:
Alarm – Anything that comes from the SIEM, IPS, or Endpoint solution that is notifying you of a potential threat, security risk, or operational problem.
Alert – A notification from which an analyst will determine if the Alert needs to be converted to a case, merged with an existing case, or closed as a false positive or “noise.”
Analyzer – When an Observable is detected, analysts may run tools called Analyzers to automatically gather intelligence about that particular piece of data.
Case – When an Alert requires investigation or work, the Alert is converted into a Case. Within a Case, tasks can automatically be generated within the Analyzer.
Breach – A verified incident that results in information being accessed, disclosed, or exposed.
Event – An occurrence that may go against your company’s security policy or result in unauthorized activity.
Log – A recorded activity taking place in your company’s cyber environment. Logs may originate from your security controls and network infrastructure. Essentially a record of every contact or touch made in your systems.
Observable – Key data points that are identified in an Alarm that allow an analyst to more quickly identify the nature of the activity in question. An Observable could be an IP Address, Domain, URL, or File Hash. IP Addresses are the most common Observable.
Incident – An event that does result in unauthorized activity or access.
Parsing – A rule created to extract data from a log to common fields by the SIEM.
Risk – The likelihood of a threat to enact a certain amount of damage or harm.
Rules – A sequence of correlated logic from logs derived from one of more log sources that when those data points are observed the activity triggers an alarm or alert.
Threat – Event or activity with the potential to cause damage or do harm.
Use Case – A specific situation or scenario in which the product is used.
Tuning – Adjusting your alarms and rules to lessen the “static” or “noise” created by logs that do not need further review.
What Is Managed SIEM?
Cybercrime, increasing complex attack vectors, growing hordes of threat actors, shortage of security professionals, and 24x7 readiness are many of the reasons organizations are moving towards managed security providers.
Read more about how co-managed SIEM can better your team's security operations.
MANAGED SIEM OPTIONS
WHO BENEFITS
Many businesses may have a SIEM but no way to manage it or provide the workforce needed to review the SIEM’s collected logs. According to the 2019 SIEM Survey Report from AlienVault, 76% of enterprises say SIEM reduces the likelihood of a security breach and 30% of those enterprises also report a reduction in breaches overall. While SIEM can be effective in reducing the likelihood of a breach, in helping to monitor the environment, and in detecting threats, 40% of enterprises say they lack expert or trained staff to manage their SIEM.
Small In-House Teams
Businesses with a large environment but smaller staff. Those who spend more time putting out fires than completing projects and whose engineers tend to operate in a reactive mode, not proactive.
Read more about the effort difference between in-house SIEM and co-managed SIEM or how to prevent burnout in your internal teams.
Blind Teams
Businesses lacking visibility into their environment. There is limited or no central log collection, no predictable system upgrades or expansions, and likely blindsided by security or operational issues.
Future-Thinking Teams
Businesses needing to focus staff efforts on innovation, not routine tasks. Projects may drag on too long because routine and maintenance tasks tie up engineering hours.
Goal-Oriented Teams
Businesses wanting to optimize the value of their employees and focus on company objectives. We’ll discuss the varying options below as there are many ways to achieve this goal within managed services.
MANAGED SIEM OPTIONS
In-House SIEM
Organizations may recruit and train their own team to run an in-house Security Operations Center (SOC), fearing a Managed Security Services Provider's (MSSP) unfamiliarity with the business, risk of data exposure, and loss of control. However, this option can be three to five times more expensive and can result in alarm familiarity/noise, leading to important alarms being ignored. This option may be available for those companies further in their lifecycle and is often seen as an “end goal” for many security teams.
Co-Managed SIEM
An MSSP deploys SIEM from scratch or integrates it with an organization's existing security infrastructure and personnel to improve security posture. This ensures a wider security cover (knowledge of common issues across the industry) at lower cost and generally quicker deployment, depending on the customization. Co-managing also ensures the in-house team remains up-to-date and has access to state-of-the-art security tools.
This option is often seen as a partnership between a managed security services provider and the client security team, helping the client build their operations and manage long-term projects.
Multi-Tenant SIEM
This SIEM option can be compared to multiple renters living in the same apartment complex. A scalable, centralized SIEM, allows security management for multiple client instances (tenants that may be geographically distributed), allowing data segregation, role-based access, centralized upgradation, and lower costs due to shared resources. This option, however, has the disadvantage of being a single point of failure that can have a cascading effect on all tenants.
Why Co-Managed SIEM?
If you’re hiring a company to help with your company’s SIEM, you can normally choose from two options: co-managed and managed SIEM. While both solutions have their pros and cons, there’s a strong internal debate in the security community on which option is the best choice.
Companies like to choose co-managed SIEM when they have a decent in-house IT staff but lack the bandwidth to monitor alerts constantly. Such organizations often use the co-managed solution to cut operational costs while they are smaller but look to move many of the functions in-house as they mature. Co-managed SIEM is also known to be a positive step toward building a SOC within your own IT team.
Read about the healthy habits needed for a SIEM service provider relationship.
Integration
Expertise
Capacity
Customization
Lossless Transition
Common SIEM Management Features
These management and monitoring features are often offered by the co-managed service, to be performed by the co-managed service’s staff.
Real-Time Analysis
Real-time analysis is performed on critical alarms generated from the SIEM’s log correlation. Correlation is performed by the SIEM as logs are inspected to look for relationships, patterns, and trends across all log hosts to identify activity that may be malicious in origin. Actionable events will be investigated and escalated via the ticketing system and pre-determined escalation path.
Health and Performance
Monitoring of appliance health and performance.
Patch and Software Updates
When new software updates or patches are available, the co-managed team will schedule a maintenance window to perform updates.
Tuning and Configuration
Ongoing tuning to keep up with network changes as well as adding new log sources. Learn more about effectively tuning your SIEM.
Detailed On-Demand Reporting
On-demand reports detailing statistics and analysis of the activity of the hosts reporting in to the service may be available. Many of the reports are tailored to meet security or compliance requirements.
Automated Alerting
Determination of automatic alert thresholds. Automatic alerts are generated when the SIEM has identified activity as suspicious based on signatures, behavior patterns, and other algorithms.
Common SIEM Monitoring Features
Once the SIEM is fully deployed, or if the co-managed team is taking over monitoring of an existing SIEM deployment, monitoring features may then include…
Integrated Ticketing System
When actionable events are identified by the co-managed team or an automated alert is generated, all information is submitted into the ticketing system for investigation, tracking, and auditing purposes.
Log Queries and Investigation
When suspicious activity has been detected or an investigation of the activity of a host is required, the co-managed team can perform custom queries in the SIEM Log Database to retrieve event information from a designated date and time.
Availability and Outage Notifications
Availability of the equipment is monitored 24x7. In the event that the device, becomes unreachable, an investigation will take place.
Co-Managed SIEM Offerings
Most SIEM features and further service offerings available for a fully outsourced managed SIEM may also be available in a co-managed SIEM service. You can read more about the differences between fully managed and co-managed SIEM here.
Content and Offense Rules
Packaged Use Cases
Advanced Intelligence
Security Orchestration, Automation, and Response (SOAR/Smart Response)
Analyst/Engineer Complementary Skillsets and Certifications
Dashboarding Visualization
Service Desk Integration
SIEM Capability Build-Out
HOW IS SIEM MANAGED?
This is an example workflow that details the beginning and ongoing stages of co-managed SIEM. Further ongoing activities are listed in the management and monitoring features.
(Read more about what can delay your SIEM deployment.)
We’ve used the RedLegg process as the framework here. Other co-managed services may differ in their processes.
PHASE 1:
ONBOARDING
PHASE 2:
CAPACITY
BUILDING
PHASE 3:
BASELINING
PHASE 4:
TUNING
PHASE 5:
ONGOING SERVICE
PHASE 1:
KICKOFF & ONBOARDING
The co-managed team holds a kickoff call with you and the assigned personnel for the engagement:
- Deployment Engineer – Assists with conducting a SIEM health check when taking over an existing SIEM installation, as well as building the appropriate alarms and rules to maximize the capabilities of the system.
- Support Engineer – The assigned lead engineer for the account who will handle upgrades, patching, and making sure the SIEM is running at optimal efficiency.
During the kickoff and onboarding phase, the co-managed team discusses your needs and the service team’s capabilities for providing the best service. This includes…
- Reviewing your business and security operations
- Assigning the main project contact
- Determining the secondary client contact
- Creating initial escalation documentation
- Reviewing relevant co-managed processes and procedures
PHASE 2:
MANAGED SECURITY SERVICE CAPACITY BUILDING
During this phase, the co-managed service team assists in reviewing current log collection and, if needed, collecting additional required log sources from the network. This process helps eliminate unnecessary “noise” and provides the best information to be ingested into the SIEM. This is a significant amount of work designed to help you get the most of your SIEM installation.
- Once the proper log sources are being fed into the SIEM, the co-managed service team builds out the roles for their support and security to send operational and security alarms.
- To build out the operational alarms, the Deployment Engineer goes into the operational rules, copies each applicable operational rule, and creates a customized alert. This is done to prevent the rules from being erased during updates to the SIEM solution. These rules are then installed in the system. The operational alarms allow the co-managed service team to monitor the performance of the SIEM to make sure it is operating at its peak efficiency. Once the Deployment Engineer is sure the rules are operating correctly, alerting of these rules is turned on and monitored and is then handed off to the Security Analysts.
- While Phase 3 is in progress, the Deployment Engineer will work with you to build any additional use case alarms, custom parsers, or dashboards, or upon your request, customizing what you want to monitor and then building it.
- Some customizations may result in additional cost. The Deployment Engineer will advise whether any additional charge is necessary, and then will update and validate the escalation documentation to move the service into Phase 3.
PHASE 3:
BASELINING
During Phase 3, the co-managed service’s Security Analysts monitor the initial alerts coming into the SIEM and perform initial tuning. This helps to ensure that the alarms are operating properly, that the suppression thresholds are properly set to avoid too many alarms, and that there is no duplication. This is one danger area of SIEM installations, as the initial baselining and operational turning can be overwhelming for many organizations monitoring alerts. During this period, the co-managed service team will work with you to finalize the escalation paths and re-align the escalation plan if necessary. During Phase 3, all alert monitoring and response is performed outside of the SLAs.
PHASE 4:
OPERATIONAL TUNING
Phase 4 features the bulk of the tuning of the SIEM. Along with Phase 3, this is one of the danger areas of a SIEM, as the operational tuning can be overwhelming. During Phase 4, the co-managed service’s Security Analysts will be monitoring the alerts and investigating them. Real events will be handled according to the escalation procedure. False alarms will be tuned appropriately. During this process, the co-managed service team may be tuning down duplicate alerts, ensuring that the rules fire correctly and that the alerts are sending relevant information, and then verifying what the alarm is forwarding.
PHASE 5:
ONGOING MANAGEMENT AND MONITORING
As the false alarms subside and the SIEM alerts stabilize, the environment now has a fully functioning and tuned SIEM. The co-managed service team will continue to monitor security alerts and conduct investigations, while ensuring that the SIEM is running at peak performance. During this time, the co-managed service team will begin running quarterly business reviews, offering suggestions to help improve the services and the overall security posture.
PHASE 1:
ONBOARDING
- Deployment Engineer – Assists with conducting a SIEM health check when taking over an existing SIEM installation, as well as building the appropriate alarms and rules to maximize the capabilities of the system.
- Support Engineer – The assigned lead engineer for the account who will handle upgrades, patching, and making sure the SIEM is running at optimal efficiency.
- Reviewing your business and security operations
- Assigning the main project contact
- Determining the secondary client contact
- Creating initial escalation documentation
- Reviewing relevant co-managed processes and procedures
PHASE 2:
CAPACITY
BUILDING- Once the proper log sources are being fed into the SIEM, the co-managed service team builds out the roles for their support and security to send operational and security alarms.
- To build out the operational alarms, the Deployment Engineer goes into the operational rules, copies each applicable operational rule, and creates a customized alert. This is done to prevent the rules from being erased during updates to the SIEM solution. These rules are then installed in the system. The operational alarms allow the co-managed service team to monitor the performance of the SIEM to make sure it is operating at its peak efficiency. Once the Deployment Engineer is sure the rules are operating correctly, alerting of these rules is turned on and monitored and is then handed off to the Security Analysts.
- While Phase 3 is in progress, the Deployment Engineer will work with you to build any additional use case alarms, custom parsers, or dashboards, or upon your request, customizing what you want to monitor and then building it.
- Some customizations may result in additional cost. The Deployment Engineer will advise whether any additional charge is necessary, and then will update and validate the escalation documentation to move the service into Phase 3.
PHASE 3:
BASELINING
PHASE 4:
TUNING
PHASE 5:
ONGOING SERVICE
PHASE 1:
KICKOFF & ONBOARDING
The co-managed team holds a kickoff call with you and the assigned personnel for the engagement:
During the kickoff and onboarding phase, the co-managed team discusses your needs and the service team’s capabilities for providing the best service. This includes…
PHASE 2:
MANAGED SECURITY SERVICE CAPACITY BUILDING
During this phase, the co-managed service team assists in reviewing current log collection and, if needed, collecting additional required log sources from the network. This process helps eliminate unnecessary “noise” and provides the best information to be ingested into the SIEM. This is a significant amount of work designed to help you get the most of your SIEM installation.
PHASE 3:
BASELINING
During Phase 3, the co-managed service’s Security Analysts monitor the initial alerts coming into the SIEM and perform initial tuning. This helps to ensure that the alarms are operating properly, that the suppression thresholds are properly set to avoid too many alarms, and that there is no duplication. This is one danger area of SIEM installations, as the initial baselining and operational turning can be overwhelming for many organizations monitoring alerts. During this period, the co-managed service team will work with you to finalize the escalation paths and re-align the escalation plan if necessary. During Phase 3, all alert monitoring and response is performed outside of the SLAs.
PHASE 4:
OPERATIONAL TUNING
Phase 4 features the bulk of the tuning of the SIEM. Along with Phase 3, this is one of the danger areas of a SIEM, as the operational tuning can be overwhelming. During Phase 4, the co-managed service’s Security Analysts will be monitoring the alerts and investigating them. Real events will be handled according to the escalation procedure. False alarms will be tuned appropriately. During this process, the co-managed service team may be tuning down duplicate alerts, ensuring that the rules fire correctly and that the alerts are sending relevant information, and then verifying what the alarm is forwarding.
PHASE 5:
ONGOING MANAGEMENT AND MONITORING
As the false alarms subside and the SIEM alerts stabilize, the environment now has a fully functioning and tuned SIEM. The co-managed service team will continue to monitor security alerts and conduct investigations, while ensuring that the SIEM is running at peak performance. During this time, the co-managed service team will begin running quarterly business reviews, offering suggestions to help improve the services and the overall security posture.
SIEM SERVICE TEAM STAFFING
When partnering with a co-managed security service, the service may provide staffing for three areas of the SIEM management and monitoring process.
- SECURITY TEAM
- OPERATIONS TEAM
- DEPLOYMENT TEAM
SECURITY TEAM
- SLAs for all security alarms
- 24x7 on-shift presence
- Threat analysis
- Basic troubleshooting and configuration
- Support calls and tickets
Your service may provide a team of Information Security engineers. You may be assigned a lead engineer and a team of operations engineers. We will also have a deployment lead as part of our onboarding assigned to the project.
Co-managed service team members may have multiple certifications. A co-managed service may provide individual tracks for all engineers that include peer-to-peer training, industry certificates, vendor training and certificates, as well as general purpose and customer service
OPERATIONS TEAM
- Customer SMEs
DEPLOYMENT TEAM
- Product subject matter experts
- Advanced product support
- Deployment Lead Engineers
- SECURITY TEAM
- SLAs for all security alarms
- 24x7 on-shift presence
- Threat analysis
- Basic troubleshooting and configuration
- Support calls and tickets
- OPERATIONS TEAM
- Customer SMEs
- DEPLOYMENT TEAM
- Product subject matter experts
- Advanced product support
- Deployment Lead Engineers
Your service may provide a team of Information Security engineers. You may be assigned a lead engineer and a team of operations engineers. We will also have a deployment lead as part of our onboarding assigned to the project.
Co-managed service team members may have multiple certifications. A co-managed service may provide individual tracks for all engineers that include peer-to-peer training, industry certificates, vendor training and certificates, as well as general purpose and customer service
ARTICLES FOR FURTHER READING
-
-
- Managed Security Services: Rumor vs Truth
- 9 Ways To Improve Your SIEM Investigations
- How To Operationalize Your SIEM
- Tune Down The Noise: How To Effectively Tune Your SIEM
- How to Prevent Cybersecurity Analyst Burnout
- Build Your Own SOC with Co-Managed Security Services
- Habits Of A Healthy SIEM Service Provider Relationship
- The True Cost: Managed vs Co-Managed SIEM
- Tips and Tricks for Supporting SIEM Systems
- Why Your SIEM Deployment Is Taking Forever
- The Effort Difference: In-House vs Co-Managed SIEM
- How Co-Managed SIEM Leads to Better Security Operations
- How To Maximize Your MSS Experience
- Two Data Points Is A Trend. Three Data Points Is A Story
- Phases To Implement Operational Suppression
- Why You Shouldn't Be Managing Your Own SIEM
-
