8 min read
By: MSS Engineer
Rapid Reporting of Industry-Specific Threats
Just how many phishing threats does your organization or industry face at any one time? What about daily and monthly identification, reporting, and steps for mitigation? The current threat landscape can be overwhelming: even to security specialists equipped with the skills and tools to detect and mitigate threats, efficient translation of phishing and other Social Engineering threats into actionable item or historical reports can be a challenge.
The Attack Domains Feed
Collecting domains involved in phishing and other Social Engineering attempts is a key component of Threat Intelligence. Yet it is possible to create a spreadsheet—complete with screen shots—of all current threats that may affect your organization. The Attack Domains Feed service compiles a monthly list of known attack domains targeting your industry, uncovering malware that exploits documents, executables, and other attack tools (like fake scans) to pervade the business environment.
But perhaps your security group already knows that your industry is under attack from the likes of BankBot, Zeus, Neverquest, Gozi, Dridex, Ramnit, GozNym, Tinba, GootKit, and Qadars, among others. Since Social Engineering attempts spread at lightning speed, how can the feed be collated rapidly into an actionable list?
The scenario: The top-level .xyz domain (TLD) had over 1.5 million domain name registrations in 2015, and by mid-2016, was ranked as fourth-largest TLD after .com, .net, and .org. The .xyz TLD recently reported over 4,000 threatening domains registered to it on a single day. But even with this number of domains, it’s possible to use a tailored keyword search to quickly identify and tag specific Social Engineering attack domains across an industry:
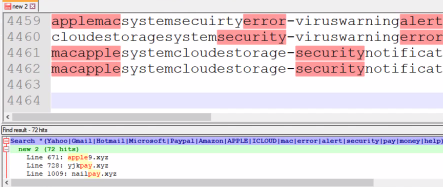
The collection: After identification, a URL Profiler application can pull specific line items from the domain search results so that those URLs can be:
- Opened for direct examination of the threat on the user (such as a fake system scan that locks the browser and tells the user that they need to call to get the malware removed) OR
- Pulled from the list for customized reporting
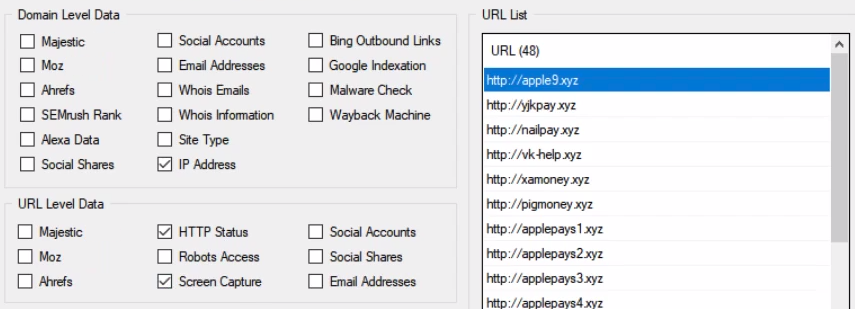
The details: Screen shots, DNS information, and HTTP status can all be easily pulled from the URL Profiler results into a spreadsheet. Now, current Social Engineering attacks across the searched domain can be readily reviewed in the spreadsheet format, making reporting easier and faster than ever.
Monthly Reporting
Based on a customized search using industry-specific keywords, monthly reports can be easily generated from the URL Profiler results to include:
- Current Social Engineering threats targeting the industry
- Highly manipulative or malicious threats and the keywords used to uncover them
Once the threats are identified, using further search techniques or common threat databases, the report can also include:
- Known remediation techniques
- How to mitigate these potential attacks before they happen
RedLegg Solutions
As your trusted partner in security, RedLegg offers both Social Engineering Awareness and Managed Security Services (MSS) teams.
Social Engineering
RedLegg's Social Engineering campaigns simulate phishing attacks via phone and email, an effective way of establishing your organization’s level of awareness. Campaigns can be customized for each client, based on current or anticipated threats and level of awareness. RedLegg's execution, consistency, data capture, and intelligent linking of phone calls, emails, training, and games can be an integral part of your security awareness strategy.
Managed Security Services
The US-based MSS team has over 20 years of collective cybersecurity experience, and quickly detects and responds to threats that affect your core business, including monthly reporting. RedLegg MSS offers:
- Unified Threat Management
- Managed and Monitored SIEM
- Advanced Threat Defense Services
- Endpoint Protection





