9 min read
By: RedLegg Blog
What is RedLegg's Analysis Platform?
A tool designed by the RedLegg Threat Research Team, RedLegg's Analysis Platform allows RedLegg Managed Security Services to better manage, investigate, and contextualize intelligence around security threats identified in live real-world environments. MSS Security Analysts provide next level Threat and IOC
READ ABOUT THE PLATFORM'S STORY
WHAT IT DOES:
- Case Management System – Correlate tasks, observables, and alerts into a single investigated case to better track and document an event.
- Threat Analysis Tools –
Built in automated and on-demand analyzers allow analysts to quickly and easily gather information and intelligence onthe the observables identified. Cross-Custome r Correlation –High level visibility into potential threats that may be affecting multiple customers.- Observable Management – Automatic extrapolation of key data points that direct an analyst to quickly identify a security alert
Work flow Standardization – Tasks and workflow are automatically presented to analysts in playbooks when new cases are created. This assures consistency and thorough research- Asset Management – Critical customer assets are tagged by engineers with context so they can be quickly identified in subsequent
- Malware Sandboxing – Malicious files and IPs forwarded to the Analysis Platform can be detonated safely in our sandbox environment and results/intel gathered
provide a more thorough investigation. - Security Focused - Security and operational alarms are separated to keep staff focused on the alerts that pose the biggest risk to a customer’s business
. Threa t Intel Ecosystem – The observables are gathered and curated before being and submitted to the = RedLegg Threat Intel Feed for use in subscribing customer SIEM environments.
KEY DIFFERENTIATORS:
CORRELATION - RedLegg's Analysis Platform is unique from a Managed Security Service perspective because it allows us to not only perform case management and threat analysis from a centralized
INTELLIGENCE – We put the threat data that our analysts gather from investigations back to work into our Threat Intelligence Service. This gives our subscribing customers a leg up on staying on top of real-world potential risks that may affect their business vertical. The Analysis Platform – Threat Intel Ecosystem is unique in Managed Service Providers as we use real threat research to make the process smarter.
OBSERVABLES AND ASSET MANAGEMENT – Part of the challenge in identifying a security threat is know what the hosts participating in the activity are. With our observable analyzers and our custom asset management, we can notate known customer hosts as well gather quick intel on potential external threats.
All of these differentiators serve to provide a better customer deliverable by enabling our analysts to provide better analysis, quicker identification of threats, and ability to be proactive with identifying and mitigating known threats through threat intelligence.
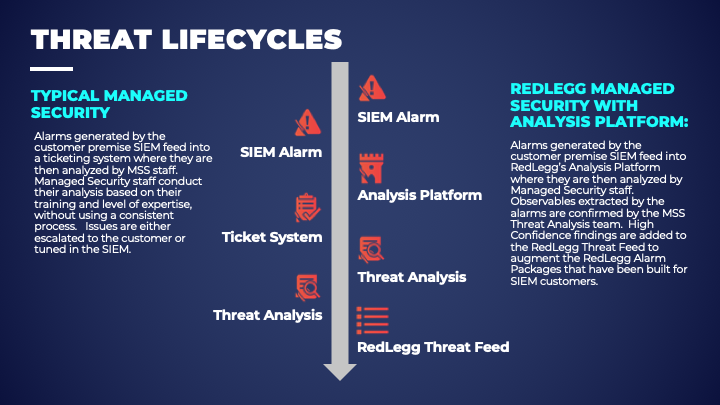
Analysis Platform's Threat Intel Ecosystem:
Customer Alarm - An alarm is generated from a monitored customer environment. The alarm sends directly to Watchtower as an Alert
Analysis Platform - Within the Alert, the platform identifies and extracts Observables – IP Address, Domain, URL, or File Hashes
Threat Analysis - Analysts review the Alert data and run investigations on the identified observables, Analysts report their findings to customers and submit observables to the Threat Research team for review
Threat Intelligence Service - Observables are reviewed by the Threat Research team to verify their validity as bad actors